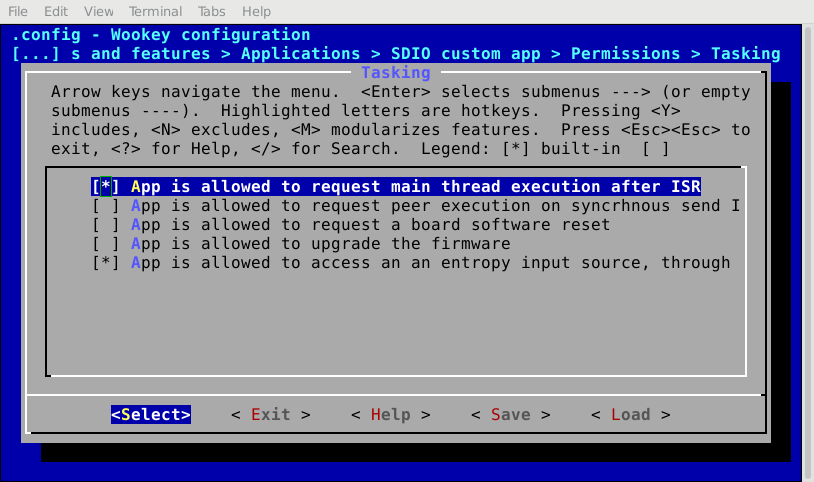
5.3.3. EwoK permissions¶
Contents
5.3.3.1. General principle¶
Permissions are statically set at configuration time, before building the firmware, and cannot be updated during the device life-cycle. Each application permission is stored in a .rodata part of the kernel, reducing the risk of any tampering with.
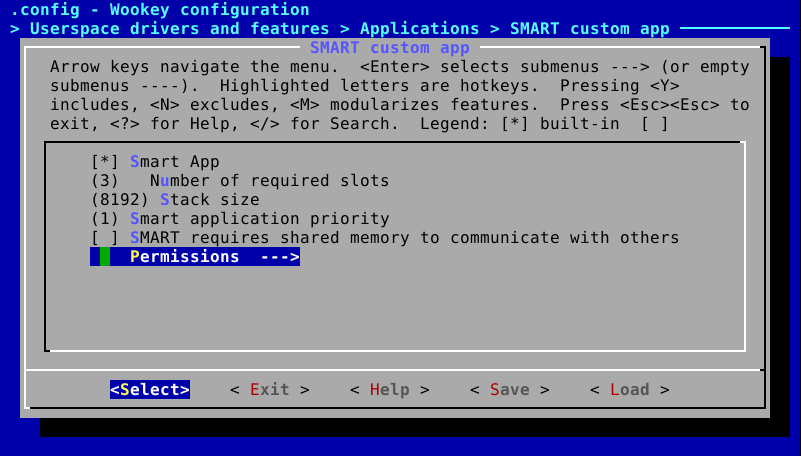
5.3.3.2. Configuring the permissions¶
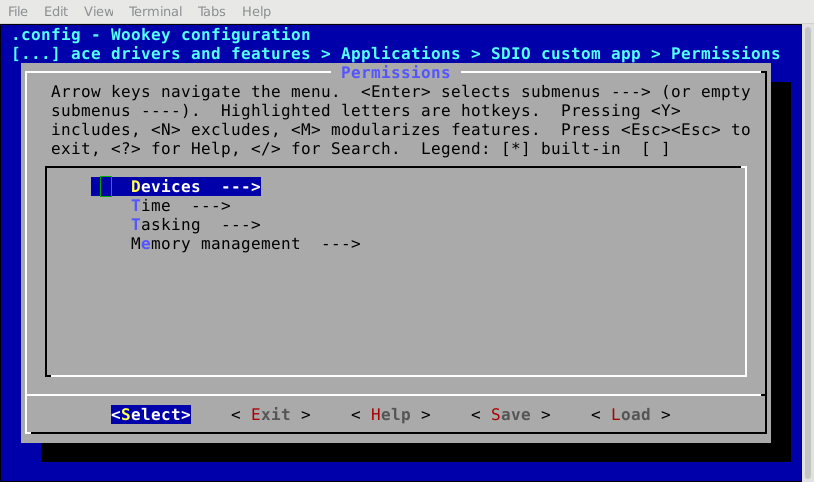
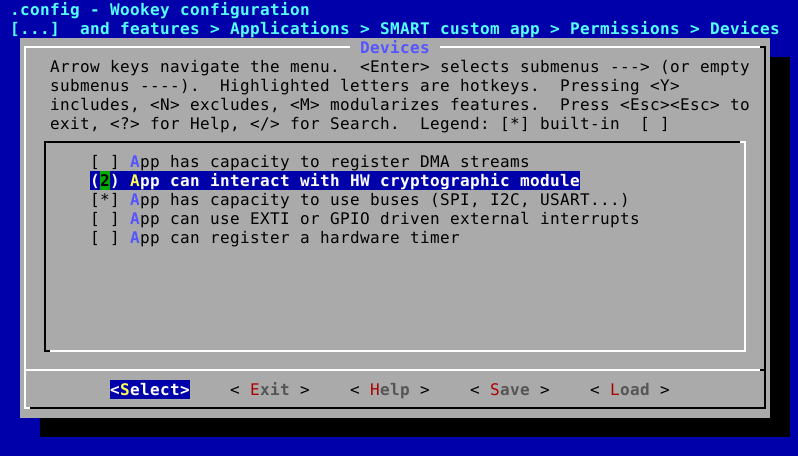
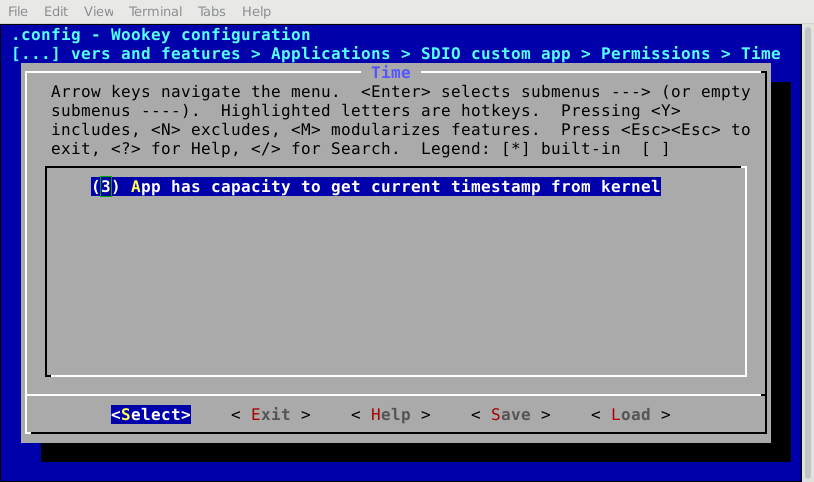
Permissions are configured by using two complementary means:
- The whole permissions, except IPCs, are set using
menuconfig- IPCs are configured by editing
apps/ipc.configandapps/dmashm.configfiles
5.3.3.2.2. IPCs¶
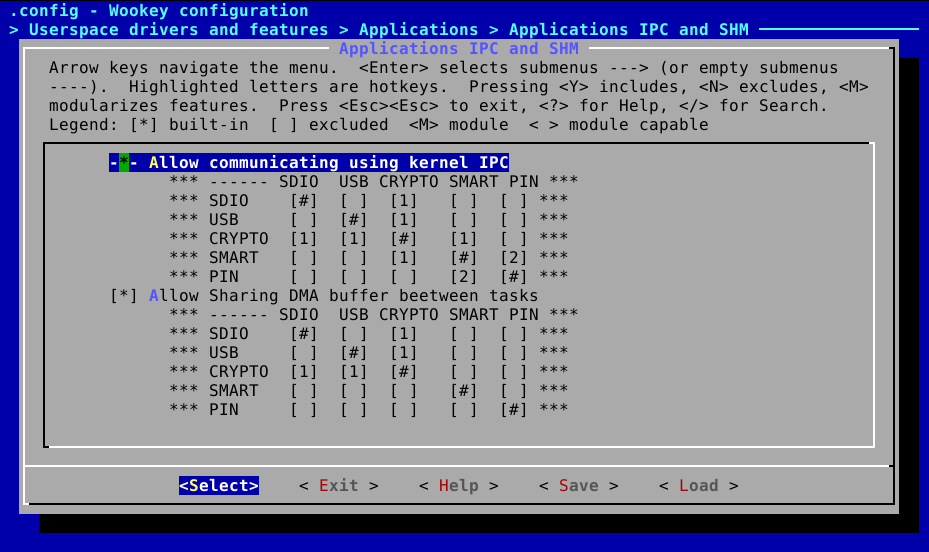
Communication permissions are based on two arrays, found in plain-text files:
- The array in
apps/ipc.configis used to set the permissions for using the IPC mechanism- The array in
apps/dmashm.configis used to set the permissions for using the DMA shared memory mechanism
IPC array is in apps/ipc.config. The sender is on the left column. Setting
1 in a box means that the task on the left is able to send a message
using IPCs to the one above:
comment "------ SDIO USB CRYPTO SMART PIN"
comment "SDIO [#] [1] [ ] [ ] [ ]"
comment "USB [ ] [#] [ ] [ ] [ ]"
comment "CRYPTO [ ] [ ] [#] [ ] [ ]"
comment "SMART [ ] [ ] [ ] [#] [ ]"
comment "PIN [ ] [ ] [ ] [ ] [#]"
Warning
A task is not allowed to send IPC to itself
DMA shared memory array is in apps/dmashm.config. The “caller” is
on the left column. A mark in a box means that the task on the left (the
“caller”) is able to share a buffer with another task (the “granted”). The task
selected on the right columns are granted to use a buffer in “caller” address
space for DMA transfers:
comment "------ SDIO USB CRYPTO SMART PIN"
comment "SDIO [#] [ ] [ ] [ ] [ ]"
comment "USB [ ] [#] [ ] [ ] [ ]"
comment "CRYPTO [ ] [ ] [#] [ ] [ ]"
comment "SMART [ ] [ ] [ ] [#] [ ]"
comment "PIN [ ] [ ] [ ] [ ] [#]"
Note that menuconfig displays those arrays, but without the possibility to modify them: you will have to edit the associated files manually.
Warning
A task is not allowed to delcare DMA SHM to itself